PLATFORMSUCCESS, TERM MODULES
REAL-TIME NETWORK MONITORING, MANAGEMENT & PROTECTION
Our engineering passion for excellence does not stop at break/fix solutions. We have integrated best of class systems to provide visibility into how the network functions, built tools for using and managing its assets and alerting for fraud, and developed a metrics system for tickets, all in pursuit of better user experience.
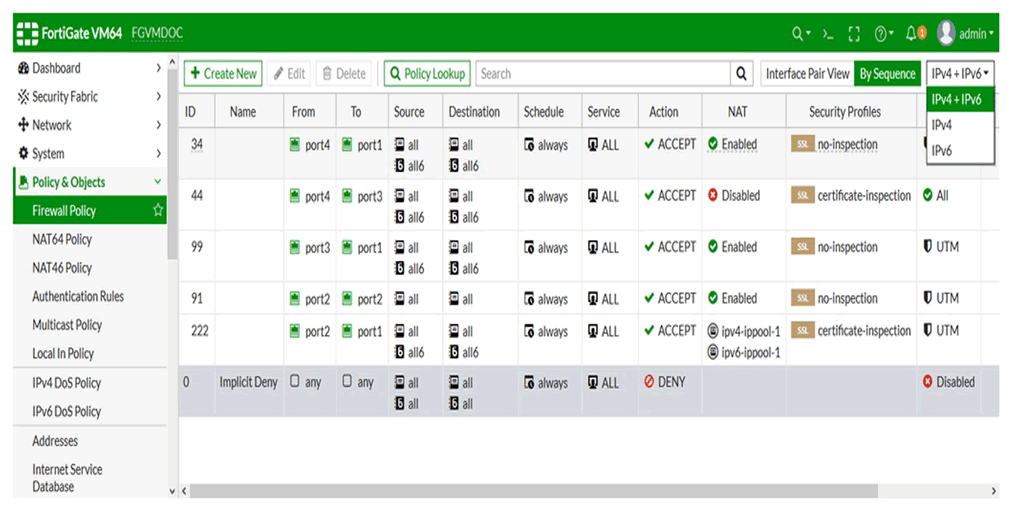
Network Security Fortinet & Kemp
The Fortinet Security Fabric continuously assesses the risks and automatically adjusts to provide comprehensive real-time protection across the digital attack surface and cycle.
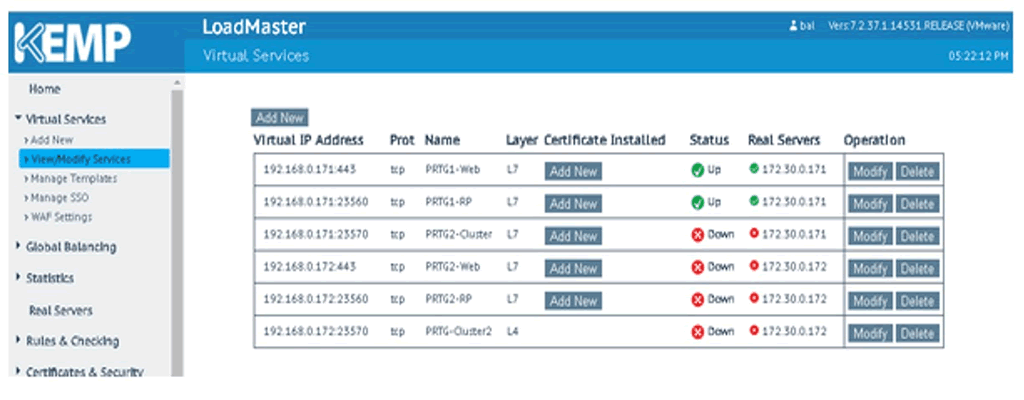
Kemp Web Application Firewall (WAF) provides continuous protection against vulnerabilities with daily rule updates based on application threat intelligence and research from information security provider, Trustwave.
Network Monitoring
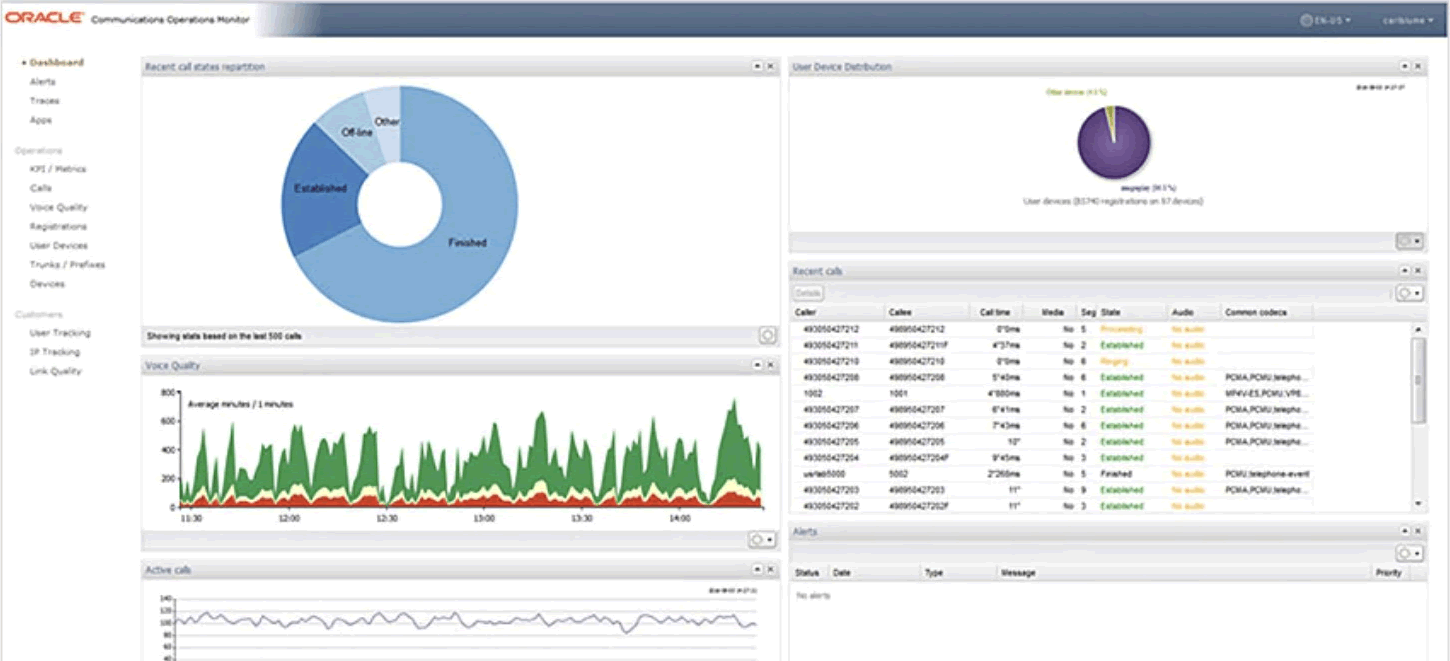
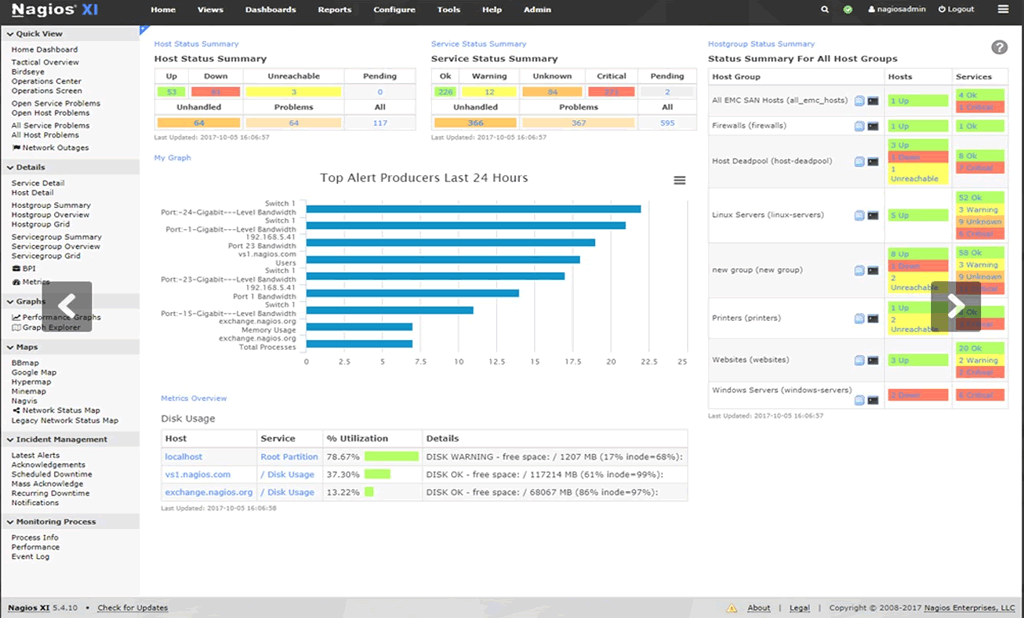
Nagios XI provides monitoring of all mission-critical infrastructure components including applications, services, operating systems, network protocols, systems metrics, and network infrastructure.
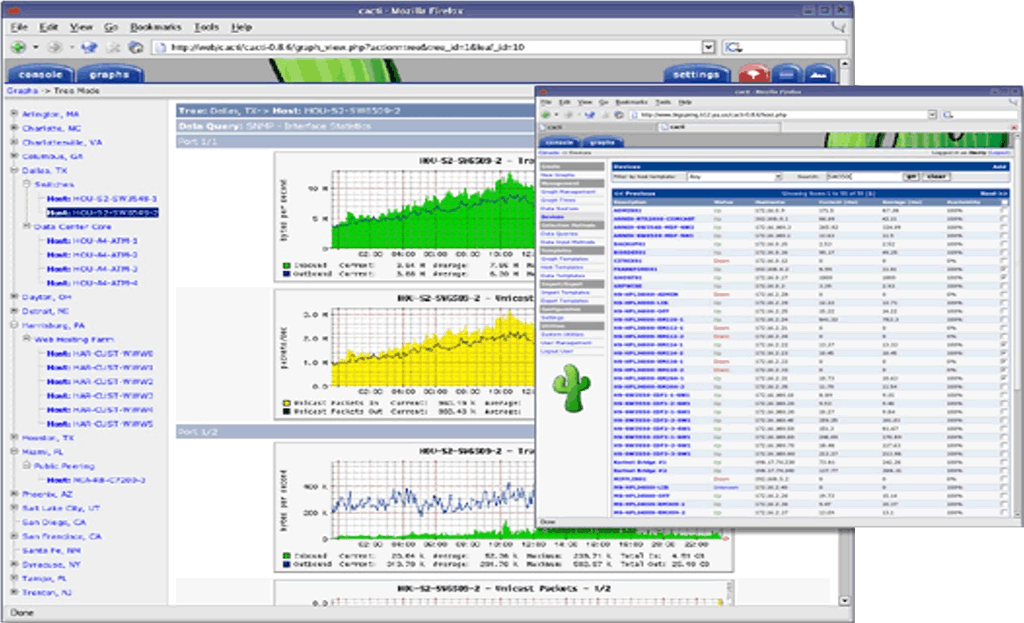
Cacti is a complete network graphing solution designed to harness the power of RRDTool's data storage and graphing functionality.
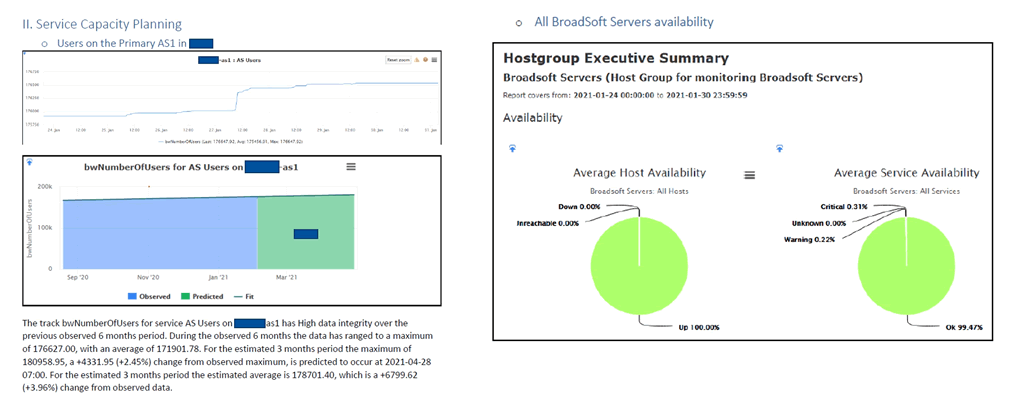
Network Availability & Capacity Management
AveriStar Severity and Escalation Guidelines
When you are submitting a problem to AveriStar, assign a Severity Level as follows:
Table 1. Severity Levels
| SECURITY LEVEL | DESCRIPTION |
|---|---|
| Severity 1 | An existing Network or Environment is down or there is a critical impact to End User’s business operation. End User and AveriStar both will commit full-time resources to resolve the situation. |
| Severity 2 | Operation of an existing Network or Environment is severely degraded or significant aspects of End User’s business operation are negatively impacted by unacceptable Network or Environment performance. End User and AveriStar both will commit full-time resources during Standard Business Hours to resolve the situation. |
| Severity 3 | Operational performance of the Network or Environment is impaired, although most business operations remain functional. End User and AveriStar both are willing to commit resources during Standard Business Hours to restore service to satisfactory levels. |
| Severity 4 | Information is required on AveriStar product capabilities, installation, or configuration. There is little or no impact to End User's business operation. End User and Cisco both are willing to provide resources during Standard Business Hours to provide information or assistance as requested. |
If you do not believe that adequate progress is being made regarding resolution of a properly submitted problem, we encourage you to escalate the problem according to the guidelines below.
Table 2. Escalation Guidelines
| ELAPSED TIME* | SEVERITY 1 | SEVERITY 2 | SEVERITY 3 | SEVERITY 4 |
|---|---|---|---|---|
| 1 Hour | TAC Team Lead | |||
| 2 Hours | TAC Manager | |||
| 4 Hours | TAC Director | TAC Team Lead | ||
| 5 Hours | TAC Manager | |||
| 12 Hours | TAC Director Second Alert | |||
| 24 Hours | TAC Vice President/Sr. Vice President | TAC Sr. Manager/Director | ||
| 48 Hours | CEO | TAC Vice President/Sr. Vice President | ||
| 72 Hours | TAC Manager | |||
| 96 Hours | CEO | TAC Sr. Manager/Director | TAC Manager |
* Severity 1 and 2 escalation times are measured in calendar hours — 24 hours per day, 7 days per week. Severity 3, and 4 escalation times correspond with Standard Business Hours.
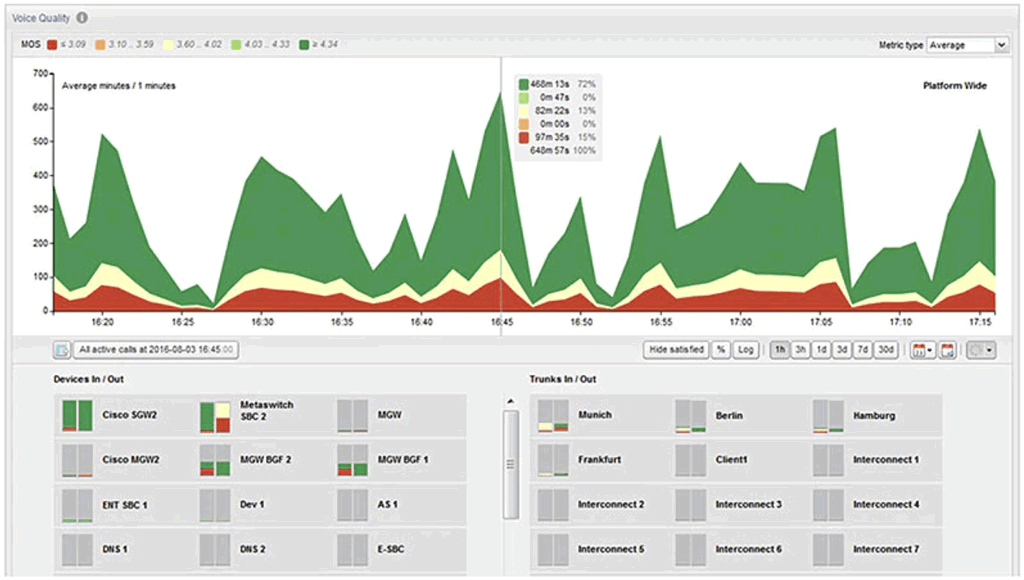
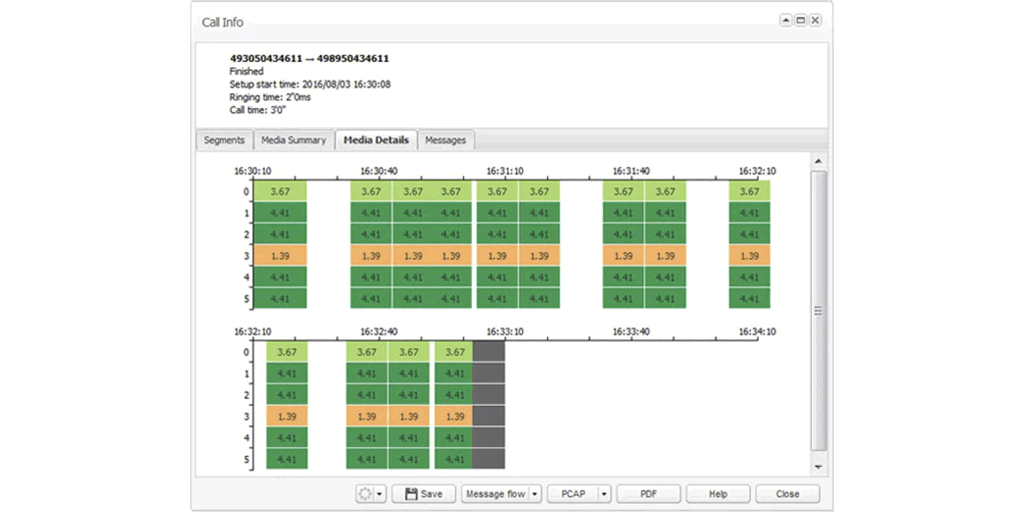
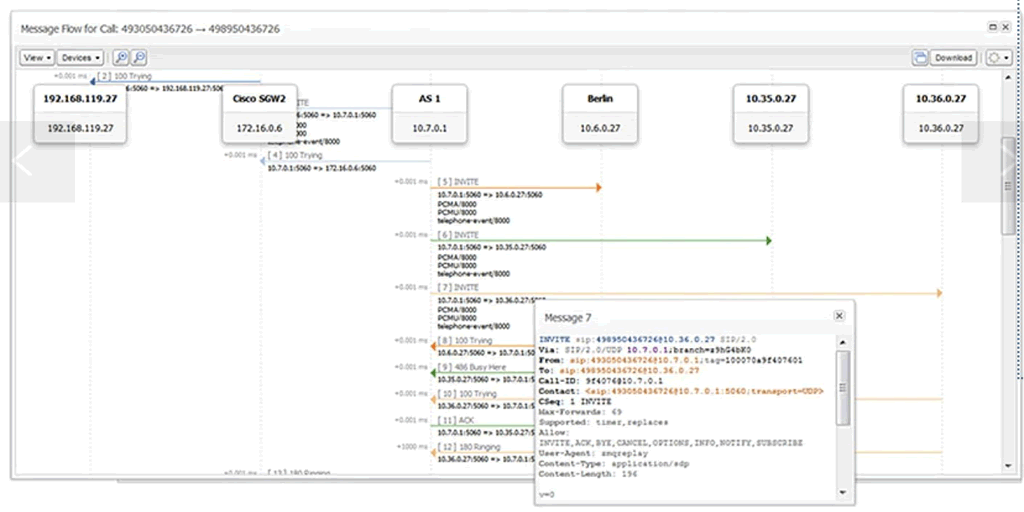
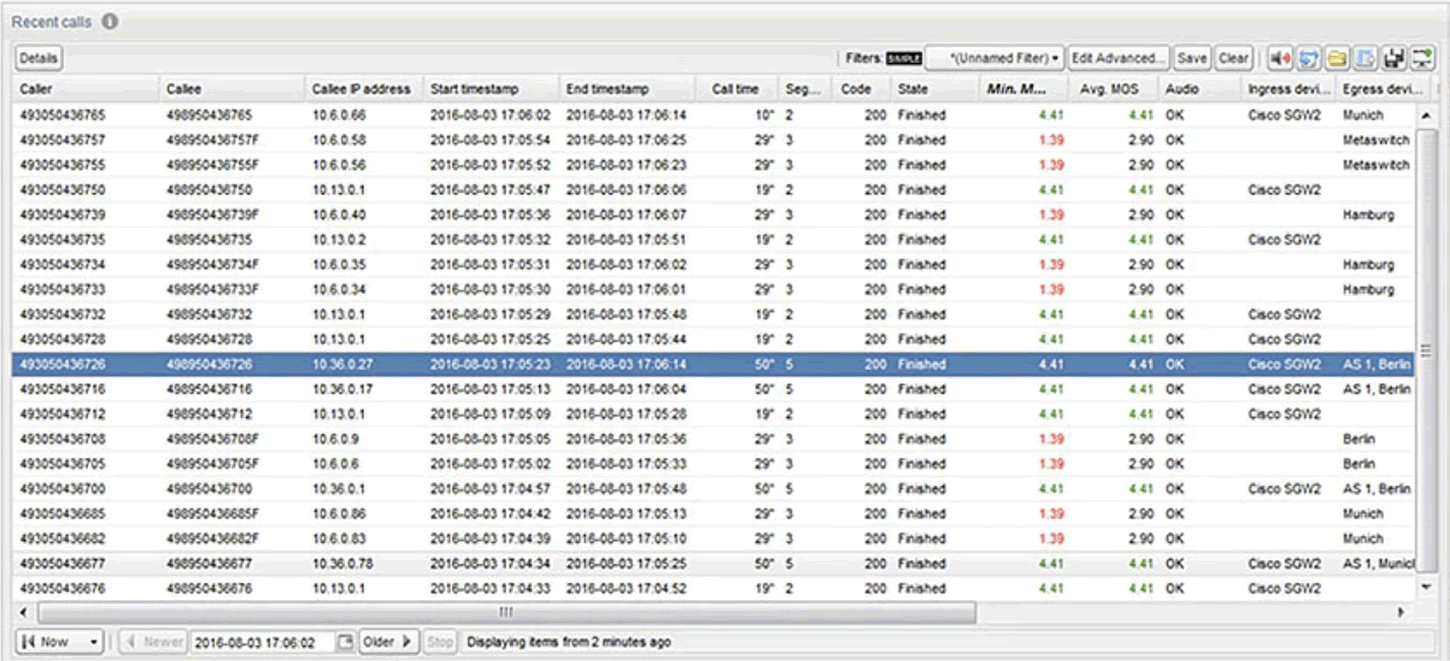
VoIP Monitoring
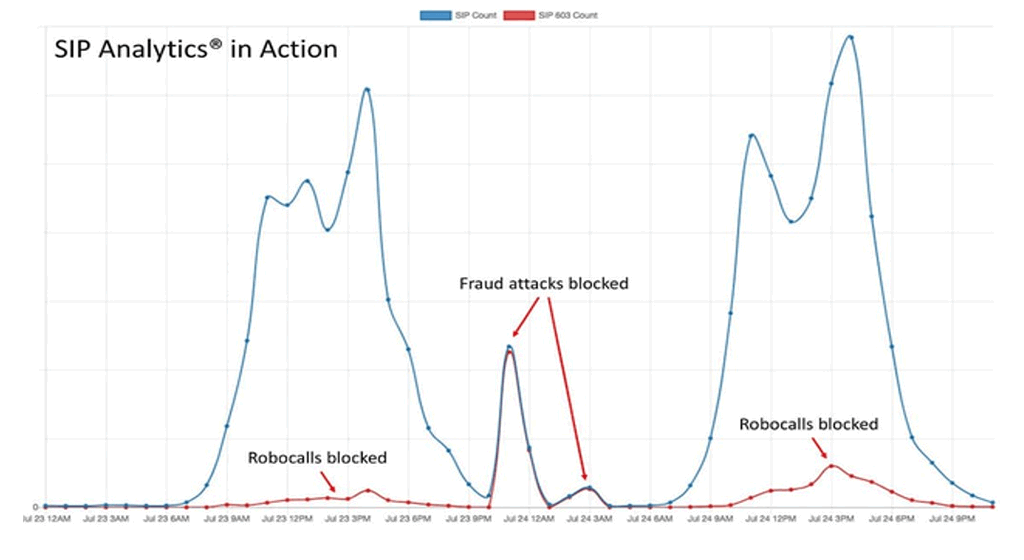
VoIP Fraud Management
SIP Analytics® inspects each call before it begins. It’s the fastest way available to detect and prevent telecom fraud.
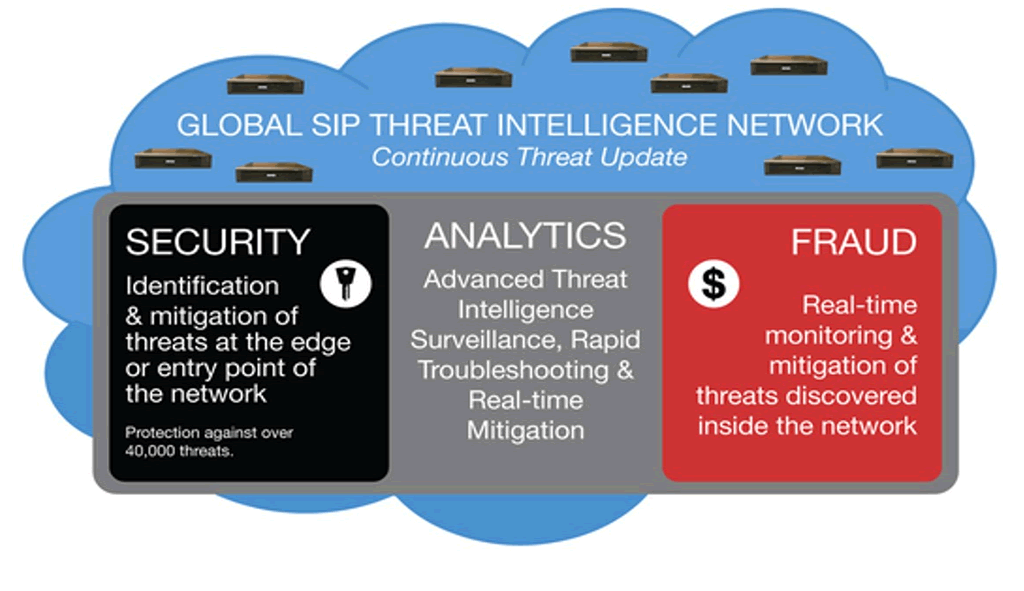
Express Management Portal
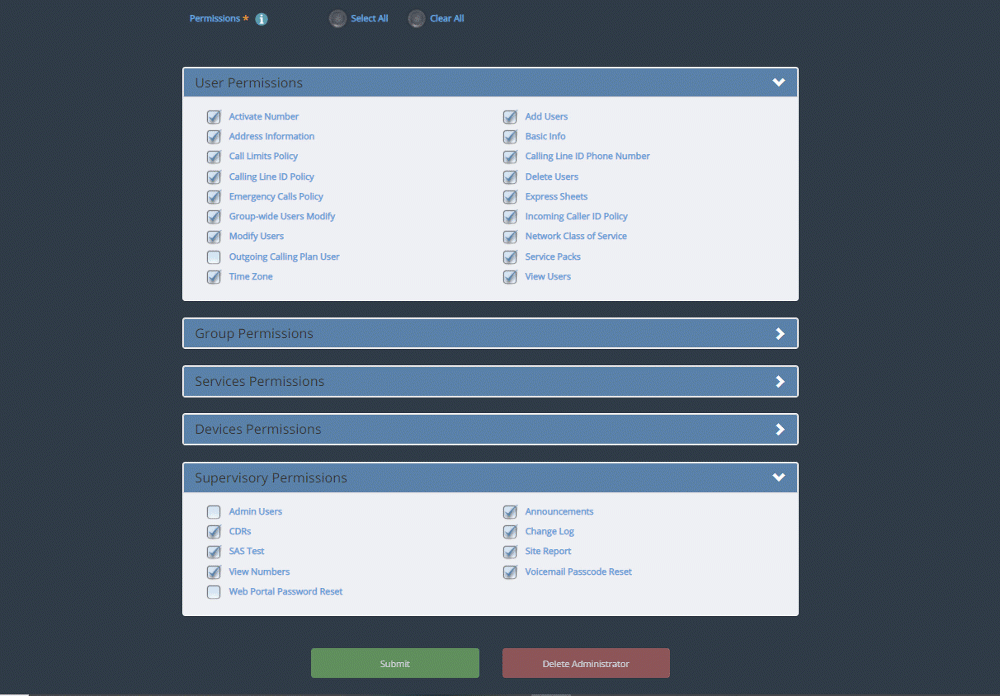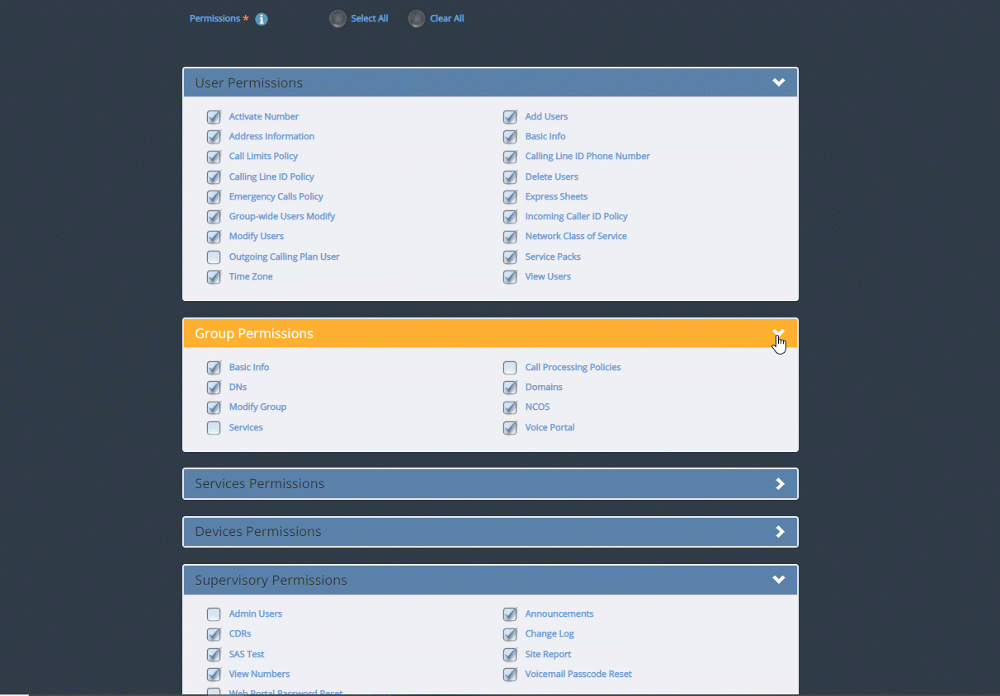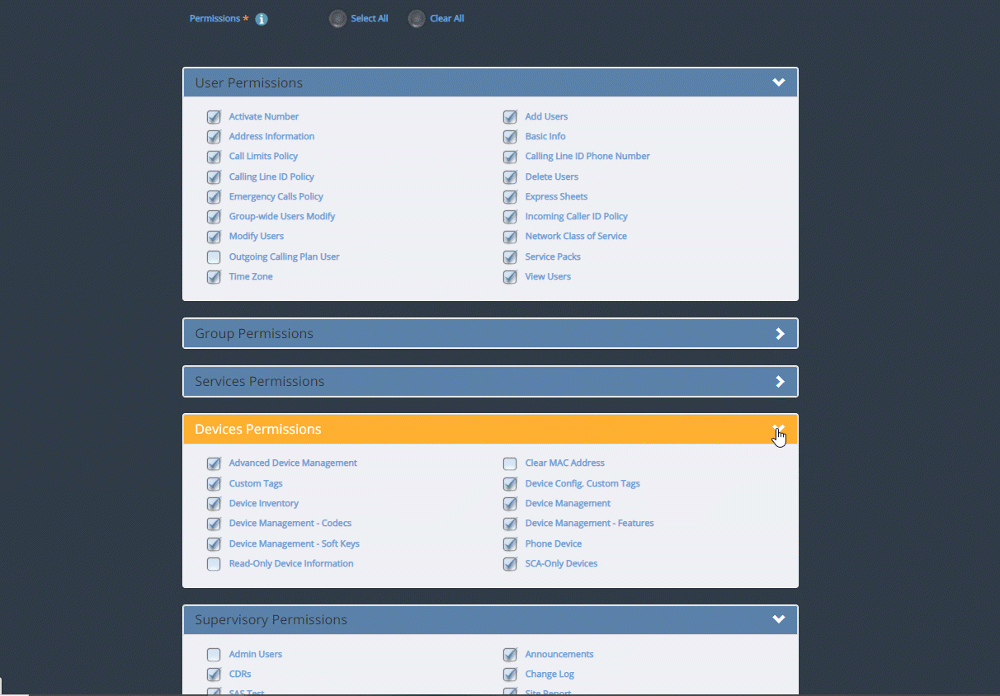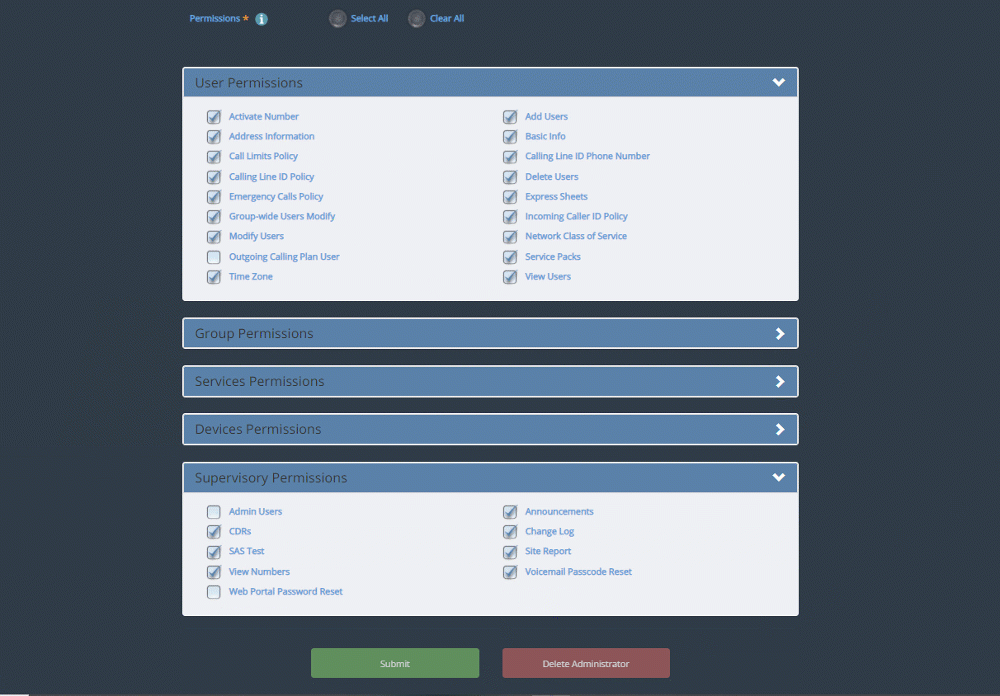

Express End User Portal